What Are the Best Open-Source Web Security Testing Tools?
What Are the Best Open-Source Web Security Testing Tools?

As security risks increase, open-source security testing programs become more crucial to organizations of all sizes. While not all open-source programs are created equal, it is essential to be considered your web security strategy. We have listed the top open-source web security testing tools for web applications.
What is Security Testing?
Testing of an application to find vulnerabilities is called as security testing. It is a type of Non-Functional Testing.
The Purpose of Security Testing is to identify or uncover any Security Loopholes (i.e. Vulnerabilities or Security Bugs) in the given Software System (i.e. Applications, Databases, Machines, Operating Systems, Organizations, etc.) and get them fixed, with an intention of protecting the information in these systems from Hackers.
Security Testing find-out whether the data and resources the data and resources related to the given Software System is protected from possible hacking/breaches/intrusions.
These are the best open-source tools for security testing
- Zed Attack Proxy (ZAP)
- WFuzz
- Wapiti
- SonarQube
- SQLMap
- Zed Attack Proxy (ZAP)
ZAP or Zed Attack Proxy is a multi-platform, open-source web application security testing tool. Developed by OWASP (Open Web Application Security Project). It is used to finding the number of security vulnerabilities in a web app during the development as well as the testing phase. ZAP is written in Java.- Advantages of ZAP: –
- ZED List out all possible vulnerabilities from your application.
- It has provided a solution to developer for preventing vulnerabilities within an application with reference websites.
- It can be help to scan all the pages and highlight the affected area of the code by vulnerability.
- It provides facility to generate report of vulnerabilities in various formats.
- Disadvantages of ZAP: –
- Lack of Proper authentication with backend systems
- Lack of access control over connections to backend systems
- Lack of proper validation and encoding of data sent to and received from backend systems
- Lack of proper error handling surrounding backend connections.
- Working of ZAP
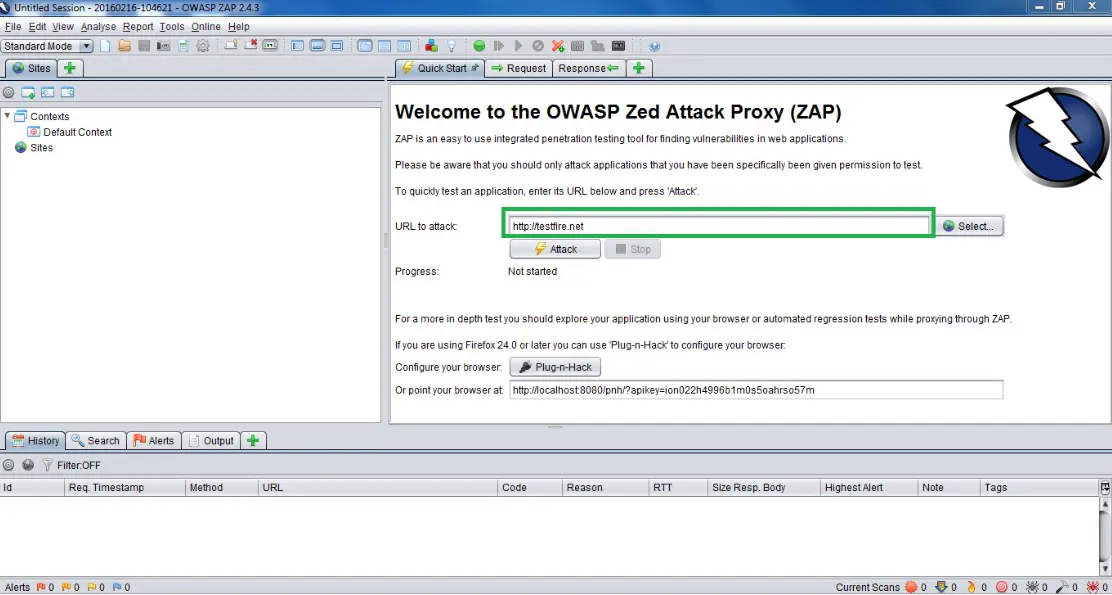
- Step 1:Enter the attack URL in “URL to Attack” text box.

- Step 2:Now click on Attack button
- Step 3:ZAP will automatically scan the web application and generate the alert report with list of possible vulnerabilities for your application.
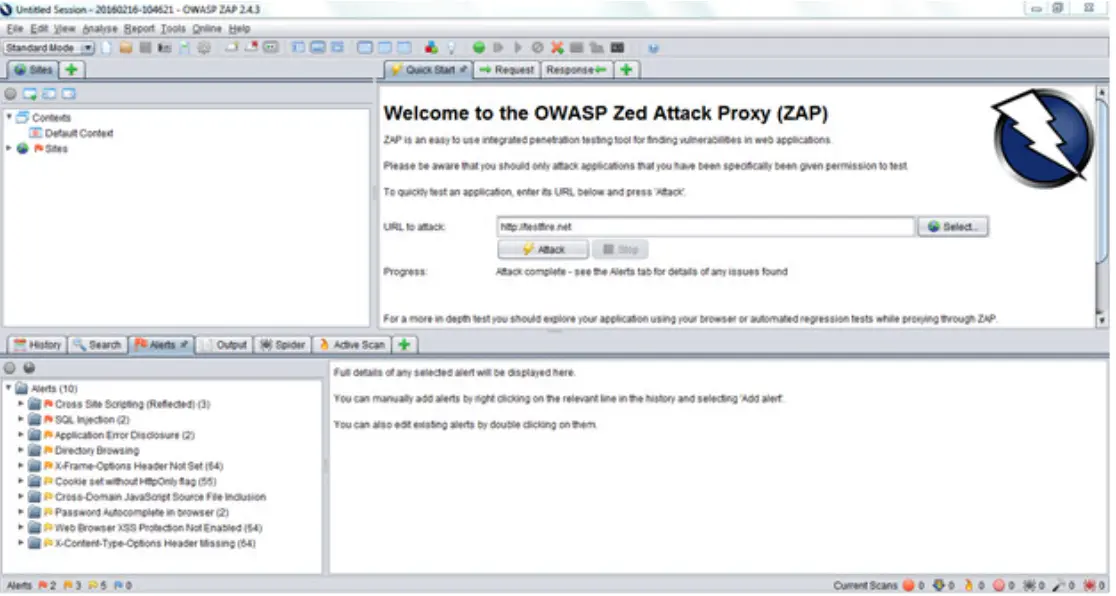
- Step 4:After exploring any of the vulnerability from Alert tab, ZAP will provide details of that vulnerability and shows the affected area of the code by highlighting the code as shown in below.

- Step 5:It will also provide detail description of vulnerability and a solution for developer with reference website(s) to prevent that attack as shown in below screen shots.

- Step 1:Enter the attack URL in “URL to Attack” text box.
- Advantages of ZAP: –
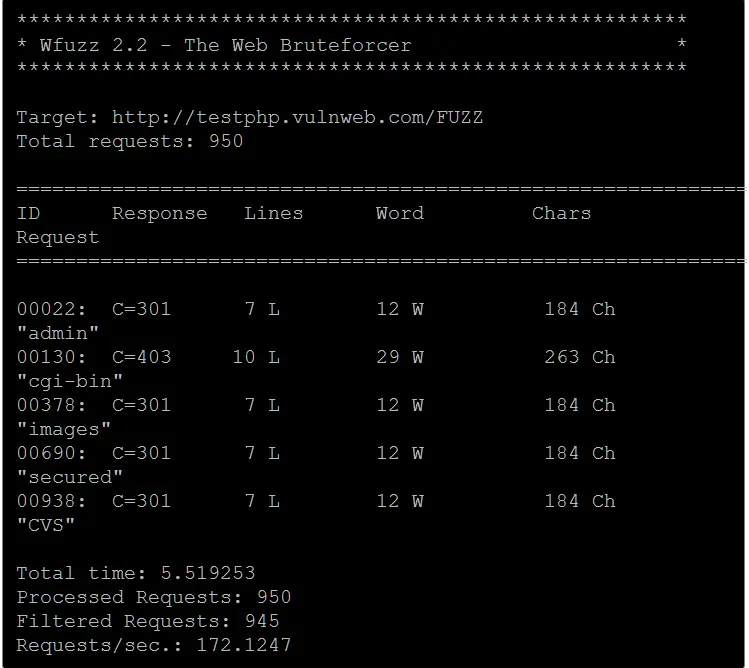
- WFuzzWFuzz is popularly used for brute-forcing web applications. It is developed in python language. It is the open-source security testing tool that has ntino GUI. Wfuzz, which is a command line tool in python uses fuzzing method to discover vulnerabilities in web application. Fuzzing determines whether any inputs comprise the web application by trying different vulnerable inputs.
- Advantages of WFuzz:-
- Wfuzz is commonly used for application fuzzing, application security, application testing, or web application analysis.
- Target users for this tool are developers and pentesters.
- Working of ZAP
- Advantages of WFuzz:-
- WapitiWapiti is command line web application vulnerability tool which performs a black box scan to audit the security of the web application. It only scans the web pages of the deployed application, not the source code.
- Advantages of Wapiti: –
- It generates vulnerability reports in various formats (HTML, XML, JSON, TXT…)
- It can suspend and resume a scan or an attack
- It can give you colors in the terminal to highlight vulnerabilities.
- It is fast and easy way to activate/ deactivate attack modules.

- Advantages of Wapiti: –
- SonarQubeSonarQube is an open-source software quality platform developed by SonarSource which continuously inspect the code quality by doing static code analysis. It provides a detail report of vulnerabilities and bugs in the code.
- Advantages of sonarQube
- It can also be used in Android development.
- It provides fully automated analyses: integrates with Maven, Ant, Gradle, and continuous integration tools (Atlassian Bamboo, Jenkins, Hudson, etc.).
- It integrates with the Eclipse development environment
- Integrates with external tools: JIRA, Mantis, LDAP, Fortify, etc.
- Working of SonarQubeSonar uses various static & dynamic code analysis tools such as Checkstyle, PMD, FindBugs, FxCop, Gendarme, and many more to extract software metrics, which then can be used to improve software quality. Provides lots of plugins.


- Advantages of sonarQube
- SQLMap
- Advantages of SQLMap
- It is easy to use.
- It is Lightweight.
- It is readily deployable.
- It supports setting up as a router, proxy or VPN server.
- Working of SQLMap


- Advantages of SQLMap
